Tiếp nối sau phần Cloud Career Pathway – Cloud Support Engineer, mình share tiếp đáp án phần Cloud Career Pathway – Cybersecurity Specialist.
Security Basics
1) True or False.
Third-party auditors verify AWS data centers’ compliance with a variety of computer security standards and regulations.
Group of answer choices
- True
- False
2) Which region is an isolated AWS Region designed to allow US government agencies and customers to move workloads into the cloud by helping them meet certain regulatory and compliance requirements?
Group of answer choices
- US East
- US West
- US FEDCloud
- AWS GovCloud
3) AWS provides a variety of tools and features that you can use to keep your AWS Account and resources safe from unauthorized use. Which of the following features is an AWS account security feature?
Group of answer choices
- All answer choices apply
- AWS Trusted Advisor
- AWS Key Management
- IAM User Accounts
4) True or False.
The AWS Production network is segregated from the Amazon Corporate network and requires a separate set of credentials for logical access.
Group of answer choices
- True
- False
5) Amazon Web Services is responsible for protecting the global infrastructure that runs all of the services offered in the AWS cloud. This infrastructure is comprised of:
Group of answer choices
- The hardware, operational software, networking, and facilities that run AWS services.
- The facilities that run AWS services.
- The hardware and operational software
- The network and facilities that run AWS services.
Identity and Access
1) What is the difference between an IAM role and an IAM user?
Group of answer choices
- There is no difference between an IAM user and IAM role.
- An IAM role has permanent long-term credentials and is used to directly interact with AWS services. An IAM user does not have any credentials and cannot make direct requests to AWS services.
- An IAM user has permanent long-term credentials and is used to directly interact with AWS services. An IAM role does not have any credentials and cannot make direct requests to AWS services.
- An IAM role is primarily a management convenience to manage the same set of permissions for a set of IAM users. An IAM user is an AWS Identity and Access Management (IAM) entity with permissions to make AWS service requests.
2) Match the following Identity and Access Management terms to proper definition.
Group of answer choices
- Identity Federation -> a process where external identities are granted secure access to resources in your AWS account without having to create IAM users. These external identities can come from your corporate identity provider or from a web identity provider
- Temporary security credentials -> credentials valid for a specified duration and for a specific set of permissions
- AWS account alias -> a name you define to make it more convenient to identify your account
- IAM policy simulator -> a tool to help you understand, test, and validate the effects of your access control policies
3) AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources for your users. You use IAM to control who can use your AWS resources and how they can use resources. Which of the following is NOT a feature of IAM?
Group of answer choices
- Security Audit
- Multi-factor authentication
- Identity federation
- Shared access to your AWS account
4) True or False.
An IAM role can be added to an IAM group.
Group of answer choices
- True
- False
5) ____________ provides an extra level of security that you can apply to your AWS environment by using an authentication device that continually generates random, six-digit, single-use authentication codes.
Group of answer choices
- Temporary Security Credentials
- Multi-Factor Authentication
- Identity Federation
- Policy Simulator
Secure Infrastructure
1) Which of the following are Amazon VPC best practices? (Select all that apply)
Group of answer choices
- Automate the deployment of your infrastructure
- Use Multi-AZ deployments in VPC for high availability
- Use security groups and network ACLs
- Control access with IAM users and policies
2) Match the following AWS Networking terms to proper definition.
Group of answer choices
- Elastic Load Balancing -> distributes incoming application traffic across multiple targets, such as Amazon EC2 instances, containers, and IP addresses.
- Amazon CloudFront -> a global content delivery network (CDN) service that securely delivers data, videos, applications, and APIs to your viewers with low latency and high transfer speeds.
- Amazon VPC -> a logically isolated virtual network in the AWS cloud.
- Amazon Route 53 -> provides highly available and scalable Domain Name System (DNS), domain name registration, and health-checking web services.
- AWS Direct Connect -> allows you can establish private connectivity between AWS and your datacenter, office, or colocation environment.
3) An Amazon VPC can span multiple Availability Zones.
Group of answer choices
- True
- False
4) Which security features are within Amazon Virtual Private Cloud (VPC)? (Select all responses that apply)
Group of answer choices
- Routing Tables
- Security Groups
- External Gateways
- Network ACLs
5) Which three main functions does Amazon Route 53 perform? (Select all responses that apply)
Group of answer choices
- API permission setting
- Register domain names
- Check the health of your resources
- Route internet traffic to the resources for your domain
6) What is a virtual private cloud (VPC)?
Group of answer choices
- A range of IP addresses
- A virtual network dedicated to your AWS account
- An Elastic IP address
- AWS Data Pipeline
7) Fill in the blank.
______________ makes it easy to establish a dedicated network connection from your premises to AWS.
Group of answer choi
ces
ces
- Amazon Route 53
- Amazon CloudFront
- Amazon VPC
- AWS Direct Connect
8) Using the scenario below order each task as Step 1, Step 2, etc. to complete the scenario activity.
Scenario: Configure Amazon Route 53 to route traffic to your new website.
Group of answer choices
- Step 3. -> Create a Website and Upload It to Your S3 Bucket
- Step 4. -> Route DNS Traffic for Your Domain to Your Website Bucket
- Step 1. -> Register a domain
- Step 5. -> Test Your Website
- Step 2. -> Create an S3 Bucket and Configure It to Host a Website
Encryption
1) True or False.
AWS Key Management Service stores, manages and tracks your data keys.
Group of answer choices
- True
- False
2) Policies attached to an IAM identity are called ____________.
Group of answer choices
- Resource-based policies
- Key policy
- Control access policy
- Identity-based policies
3) AWS Key Management Service supports two kinds of keys. Which of the following are the keys supported by AWS Key Management Service?
Group of answer choices
- Security keys and Network keys
- Memory keys and data keys
- Master keys and data keys
- Encrypt keys and decrypt keys
4) Order the procedural steps you’d follow to create customer master keys (CMKs) in the AWS Management Console.
Group of answer choices
- Step 1 -> Sign in to the AWS Management Console and open the AWS Key Management Service (AWS KMS) console
- Step 2 -> In the left navigation pane, choose Encryption keys
- Step 3 -> Choose the appropriate AWS Region
- Step 4 -> Choose Create key
- Step 5 -> Type an alias and description for the CMK
- Step 6 -> Select IAM users, roles and other AWS accounts that can use the CMK
5) Match the following encryption and decryption terms to proper definition.
Group of answer choices
- Plaintext -> Unencrypted data
- Ciphertext -> Encrypted data
- Authenticated encryption -> Provides confidentiality, data integrity, and authenticity assurances on encrypted data
- Encryption context -> A set of key-value pairs that you can pass to AWS KMS when you call the Encrypt, Decrypt, ReEncrypt, GenerateDataKey, and GenerateDataKeyWithoutPlaintext APIs
6) Access to AWS Key Management Service requires credentials that AWS can use to authenticate your requests. The credentials must have permissions to access AWS resources. Which of the following credential types can access AWS Key Management Service?
Group of answer choices
- AWS account root user
- All answer choices apply
- IAM user
- IAM role
Monitoring and Logging
1) Match the following CloudWatch concepts to proper definition.
Group of answer choices
- Events -> indicates a change in your AWS environment
- Targets -> processes events
- Rules -> matches incoming events and routes them to targets for processing
2) Amazon CloudWatch receives and provides metrics for all Amazon EC2 instances and works with any operating system currently supported by the Amazon EC2 service. What statistics can you view and graph in CloudWatch? (Select all responses that apply)
Group of answer choices
- Sample Count
- Difference
- Sum
- Average
3) Fill in the blank.
The tool ___________ is a configuration you create in Amazon Inspector to define your assessment run.
Group of answer choices
- Assessment Template
- Security Audit
- Assessment Target
- Rules Package
4) Which of the following are methods to access CloudWatch? (Select all responses that apply)
Group of answer choices
- AWS CLI
- CloudWatch API
- Amazon CloudWatch console
- AWS SDKs
5) True or False.
AWS CloudTrail provides you immediate notification related to problems with your logging configuration through your AWS Management Console.
Group of answer choices
- True
- False
6) True or False.
You define your own rules for assessment templates with Amazon Inspector.
Group of answer choices
- True
- False
7) Match the following AWS Monitoring and Logging terms to proper definition.
Group of answer choices
- AWS CloudTrail -> a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account.
- Amazon CloudWatch -> a monitoring service for AWS cloud resources and the applications you run on AWS.
- Amazon Inspector -> an automated security assessment service that helps improve the security and compliance of applications deployed on AWS.
8) The image below describes how AWS CloudTrail service works. CloudTrail records important information about a range of account activity. Which of the following is NOT an activity reported by CloudTrail?
- Who made the request
- Services used
- Actions performed
- Resource Metadata
9) True or False.
Amazon CloudWatch does not aggregate data across regions.
Group of answer choices
- True
- False
Compliance
1) True or False.
Certifications/Attestations are performed by a third-party independent auditor.
Group of answer choices
- True
- False
2) True or False
AWS does not disclose customers’ content, unless required to do so to comply with the law or a valid and binding order of a governmental or regulatory body.
Group of answer choices
- True
- False
3) Which certification is a code of practice that focuses on the protection of personal data in the cloud?
Group of answer choices
- PCI DSS
- FedRAMP
- ISO 27001
- ISO 27018
4) What is the name of the automated compliance reporting tool, available in the AWS Management Console, you can use to review and download reports and details about more than 2,500 security controls available in AWS tools and services?
Group of answer choices
- AWS Artifact
- Amazon Inspector
- AWS Shield
- AWS Key Management
5) Which AWS service is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS?
Group of answer choices
- AWS Artifact
- AWS CloudHSM
- Amazon Inspector
- AWS Config
FINAL Assessment
1) True or False.
Certifications/Attestations are performed by a third-party independent auditor.
Gro
up of answer choices
up of answer choices
- True
- False
2) Which of the following (2) services can be used to monitor the security and compliance of your environment?
Group of answer choices
- VPC and S3
- AWS Shield and Route 53
- AWS Config and Amazon Inspector
- AWS CodeDeploy and VPC
3) True or False
AWS does not disclose customers’ content, unless required to do so to comply with the law or a valid and binding order of a governmental or regulatory body.
Group of answer choices
- True
- False
4) Which certification is a widely adopted global security standard that outlines the requirements for information security management systems?
Group of answer choices
- ISO 27017
- PCI DSS
- FedRAMP
- ISO 27001
5) Which service is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data?
Group of answer choices
- AWS Key Management Service (AWS KMS)
- Amazon QuickSight
- Amazon Inspector
- Amazon Route 53
6) True or False.
AWS Key Management Service stores, manages and tracks your data keys.
Group of answer choices
- True
- False
7) AWS Key Management Service supports two kinds of keys. Which of the following are the keys supported by AWS Key Management Service?
Group of answer choices
- Encrypt keys and decrypt keys
- Security keys and Network keys
- Master keys and data keys
- Memory keys and data keys
8) True or False.
AWS Key Management Service lets you create master keys that can never be exported from the service and which can be used to encrypt and decrypt data based on policies you define.
Group of answer choices
- True
- False
9) ______________ are IAM resources that express permissions using the IAM policy language.
Group of answer choices
- Role policies
- Managed policies
- Identity policies
- Delegation policies
10) How many IAM roles can be created per AWS Account?
Group of answer choices
- 1,000
- 5,000
- 100
- 500
11) AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources for your users. You use IAM to control who can use your AWS resources and how they can use resources. Which of the following is NOT a feature of IAM?
Group of answer choices
- Multi-factor authentication
- Identity federation
- Shared access to your AWS account
- Security Audit
12) True or False.
An IAM user is a unique identity recognized by AWS services and applications. A user can be an individual, system, or application requiring access to AWS services.
Group of answer choices
- True
- False
13) Match the following Identity and Access Management terms to proper definition.
Group of answer choices
- Identity Federation -> a process where external identities are granted secure access to resources in your AWS account without having to create IAM users. These external identities can come from your corporate identity provider or from a web identity provider
- Temporary security credentials -> credentials valid for a specified duration and for a specific set of permissions
- AWS account alias -> a name you define to make it more convenient to identify your account
- IAM policy simulator -> a tool to help you understand, test, and validate the effects of your access control policies
14) True or False.
AWS CloudTrail provides you immediate notification related to problems with your logging configuration through your AWS Management Console.
Group of answer choices
- True
- False
15) True or False.
You define your own rules for assessment templates with Amazon Inspector.
Group of answer choices
- True
- False
16) What does Amazon Route53 provide?
Group of answer choices
- A scalable Domain Name System.
- A global Content Delivery Network.
- None of these.
- An SSH endpoint for Amazon EC2.
17) True or False.
Amazon CloudWatch does not aggregate data across regions.
Group of answer choices
- True
- False
18) Which of the following are Amazon VPC best practices? (Select all that apply)
Group of answer choices
- Use Multi-AZ deployments in VPC for high availability
- Automate the deployment of your infrastructure
- Use security groups and network ACLs
- Control access with IAM users and policies
19) Using the scenario below order each task as Step 1, Step 2, etc. to complete the scenario activity.
Scenario: Configure Amazon Route 53 to route traffic to your new website.
Group of answer choices
Scenario: Configure Amazon Route 53 to route traffic to your new website.
Group of answer choices
- Step 3. -> Create a Website and Upload It to Your S3 Bucket
- Step 4. -> Route DNS Traffic for Your Domain to Your Website Bucket
- Step 1. -> Register a domain
- Step 5. -> Test Your Website
- Step 2. -> Create an S3 Bucket and Configure It to Host a Website
20) Which three main functions does Amazon Route 53 perform? (Select all responses that apply)
Group of answer choices
- Check the health of your resources
- API permission setting
- Register domain names
- Route internet traffic to the resources for your domain
21) Using the scenario below order each task as Step 1, Step 2, etc. to complete the scenario activity.
Scenario: Create a VPC and subnet, and launch a public-facing instance into your subnet. Your instance will be able to communicate with the Internet, and you’ll be able to access your instance from your local computer using SSH (if it’s a Linux instance) or Remote Desktop (if it’s a Windows instance).
Group of answer choices
Step 3. -> Launch an Instance into Your VPC
Step 4. -> Assign an Elastic IP Address to Your Instance
Step 1. -> Create the VPC
Step 5. -> Terminate the Instance
Step 2. -> Create a Security Group
Step 6. -> Release your Elastic IP address
Step 7. -> Delete your VPC
22) Which region is an isolated AWS Region designed to allow US government agencies and customers to move workloads into the cloud by helping them meet certain regulatory and compliance requirements?
Group of answer choices
- AWS GovCloud
- US West
- US East
- US FEDCloud
23) Amazon Web Services is responsible for protecting the global infrastructure that runs all of the services offered in the AWS cloud. This infrastructure is comprised of:
Group of answer choices
- The network and facilities that run AWS services.
- The hardware, operational software, networking, and facilities that run AWS services.
- The hardware and operational software
- The facilities that run AWS services.
24) Which of the following is NOT an AWS authentication credential type?
Group of answer choices
- Voice Activated Password
- Passwords
- Multi-Factor Authentication
- Access Keys
25) Which of the following is NOT an AWS Security Platform service?
Group of answer choices
Group of answer choices
- Amazon QuickSight
- Amazon VPN
- Amazon Inspector
- AWS Artifact
26) True or False
The customer has complete control and ownership over the region in which their data is physically located.
Group of answer choices
- True
- False
27) Which AWS service allows you to protect your encryption keys within HSMs designed and validated to government standards for secure key management?
Group of answer choices
- AWS Shield
- Amazon Inspector
- AWS CloudHSM
- AWS Artifact
28) AWS has developed a security assurance program that uses global privacy and data protection best practices. The AWS Assurance Program is based on the following (3) guiding practices:
Group of answer choices
- Monitoring, Validating and Securing
- Logging, Monitoring and Securing
- Validating, Demonstrating and Monitoring
- Securing, Networking and Monitoring
29) Policies attached to an IAM identity are called ____________.
Group of answer choices
- Identity-based policies
- Control access policy
- Key policy
- Resource-based policies
30) True or False.
Amazon Elastic Load Balancing allows you to identify the originating IP address of a client connecting to your servers, whether you’re using HTTPS or TCP load balancing.
Group of answer choices
- True
- False
31) AWS’s data centers are state of the art, utilizing innovative architectural and engineering approaches. Which of the following physical/environmental aspects are NOT included in data centers’ architectural and engineering approaches?
Group of answer choices
- Power Supply
- Climate and Temperature
- Health and Wellness
- Fire Detection and Suppression
32) True or False.
Data centers are built in clusters in various global regions.
Group of answer choices
- True
- False
Cyber Security Final Project v1
1) Where do I go to configure the level of access for our various employees
Which of the AWS security services below will you use to help the client configure access levels for her various employees?
- IAM
- Cognito
- WAF & …
- Directory …
- Amazon …
- Secrets Manager
2) It looks like IAM has all of the tools I need, but we have several Account Managers already and expecr to hire more as we grow, but I don’t want to configure these permissions settings every time we hire a new Account Manager. What’s the best way to handle this?
Which of the responses below will the client maintain best practices for keeping the S3 bukets secure as the business grows?
- “Create an IAM group call Account Managers, apply the permissions, and add user to it as needed.”
- “Just create a single user account called Acount Managers, apply the permissions, and share the credentials with those who need them.”
- “You will have to set these permissions for each user. Sorry about that.”
- “Create an IAM role called Account Managers, apply the permissions, and assign it to the appropriate users.”
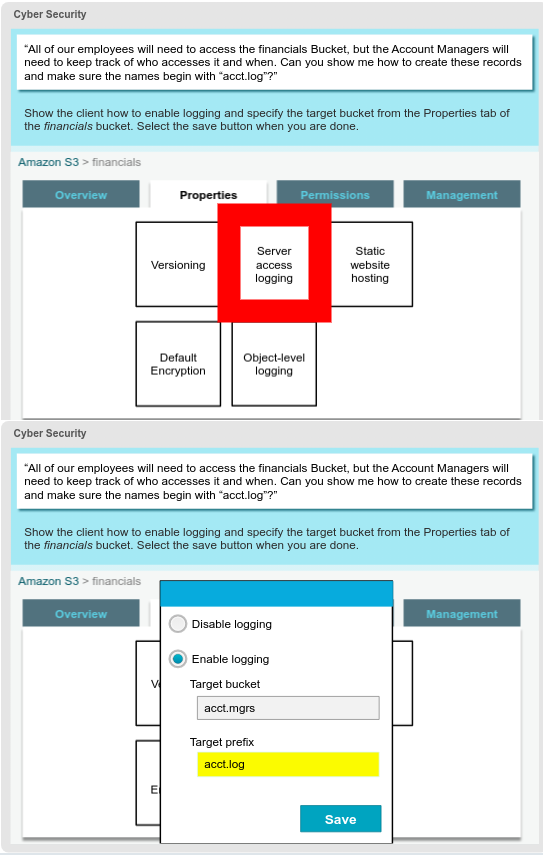
3) All of our employees will need to access the financials Bucket, but the Account Managers will need to keep track of who accesses it and when. Can you show me how to create these records and make sure the names begin with “acct.log”?
Show the client how to enable logginf and specify the target ucket from the Properties tab of the financials bucket. Select the save button when you are done.
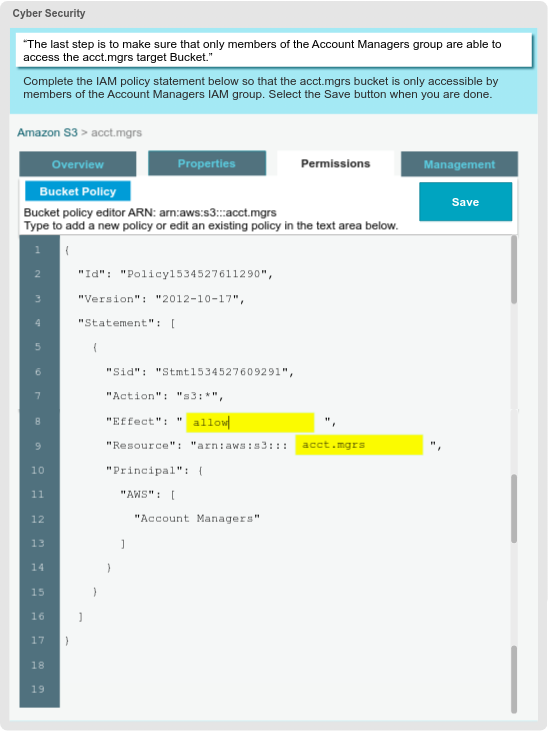
4) The last step is to make sure that only members of the Account Managers group are able to access the acct.mgrs target Bucket.
Complete the IAM policy statement below so that the acct.mgrs bucket is only accessible by bember of the Account Managers IAM group. Select the Save button when you are done.
Chúc các bạn thành công!

DienDan.Edu.Vn Cám ơn bạn đã quan tâm và rất vui vì bài viết đã đem lại thông tin hữu ích cho bạn.DienDan.Edu.Vn! là một website với tiêu chí chia sẻ thông tin,... Bạn có thể nhận xét, bổ sung hay yêu cầu hướng dẫn liên quan đến bài viết. Vậy nên đề nghị các bạn cũng không quảng cáo trong comment này ngoại trừ trong chính phần tên của bạn.Cám ơn.